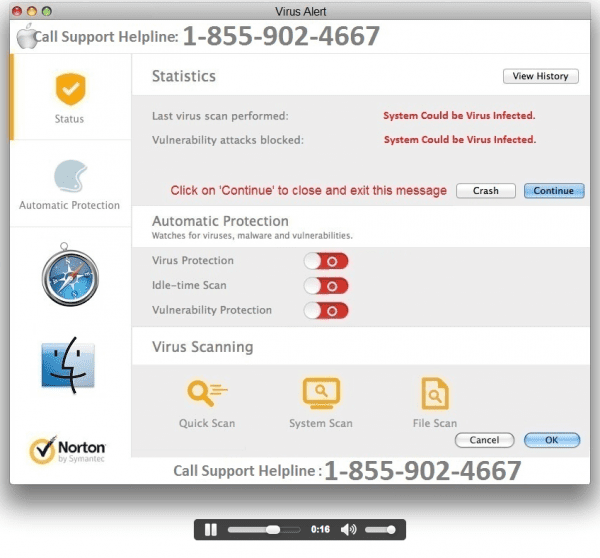
We posted yesterday about the Blackmuscats .htaccess redirection that was affecting thousands of web sites.
They are still happening (and growing), but the attackers decided to switch names to nonalco, mimosa and otherrandom keywords for their files:
1251 redirections http://fitnes-corp.ru/shurimuri?5
1093 redirections http://infofitnes.ru/interactive?5
818 redirections http://fitnes-company.ru/interactive?5
817 redirections http://mir-fitnes.ru/interactive?5
802 redirections http://info-fitnes.ru/interactive?5
788 redirections http://fitnescompany.ru/interactive?5
268 redirections http://fitnes-corp.ru/shurimuri?5
220 redirections http://infofitnes.ru/interactive?5
188 redirections http://cofitnes.ru/mimosa?5
177 redirections http://mir-fitnes.ru/interactive?5
168 redirections http://fitnes-company.ru/interactive?5
165 redirections http://info-fitnes.ru/interactive?5
162 redirections http://fitnescompany.ru/interactive?5
79 redirections http://fitnescorp.ru/shurimuri?5
40 redirections http://nashfitnes.ru/nonalco?5
37 redirections http://cofitnes.ru/mimosa?5
1191 redirections http://nashfitnes.ru/nonalco?5
981 redirections http://nash-fitnes.ru/nonalco?5
953 redirections http://supasweb.ru/blackmuscats?5
920 redirections http://nashifitnes.ru/nonalco?5
895 redirections http://nashafitnes.ru/nonalco?5
878 redirections http://nasha-fitnes.ru/nonalco?5
555 redirections http://fitnes-ltd.ru/shurimuri?5
261 redirections http://nashfitnes.ru/nonalco?5
208 redirections http://supasweb.ru/blackmuscats?5
199 redirections http://nash-fitnes.ru/nonalco?5
190 redirections http://nashafitnes.ru/nonalco?5
189 redirections http://nashifitnes.ru/nonalco?5
180 redirections http://nasha-fitnes.ru/nonalco?5
116 redirections http://fitnes-ltd.ru/shurimuri?5The redirection is still the same, going from those .ru domains, to additional second level .ru domains and themto a .pl:
http://russian-fitnes.ru/prunus/cerasus.php
http://www1.vulnerabilitytoolssolver.pl/18o8e9/al/1fedfba29dd0193d/pr2/0/
http://www1.antivirusworrydanger.pl/370l3591/al/1fedfba29dd0193d/pr2/0/
http://minimizerprocessesdebugger.pl/b6l1s/al/78dee9e271084cb2/pr2/238/
http://www1.stabilityprotectionscanner.pl/n9044s5/al/1fedfba29dd0193d/pr2/0/So far we have identified more than 17,000 sites with this type of malware. More details as we track them.